Can You Spot a Ransomware Attack Before It’s Too Late?
Ransomware is one of the greatest cybersecurity threats facing businesses today. Traditional efforts to thwart ransomware attacks focused on preventing account or endpoint compromise. Unfortunately, it’s not enough. Cybercriminals are becoming more sophisticated and successful ransomware attacks continue to rise even with these defenses in place.
It’s time to strengthen your defense.
Ransomware attacks typically include a dwell time (period between compromise and ransom execution) of a week or more. There is time to detect and stop ransomware on your network before it impacts your business. Cyber Security Shield monitors for indicators of a ransomware attack, even if endpoints are compromised, and sends you real-time alerts so you can stop the attack from spreading.
Ransomware Defense Capabilities
Prevent
List of Services
-
> Reduce Attack SurfaceList Item 1
-
> Create Zero Trust Micro-segmentation Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 2 -
> Identify IOT Risks Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 3 -
> Identify Rogue Network Devices Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 4
Detect
List of Services
-
> AD Brute Force Password AttacksList Item 1
-
> AD Account Compromise Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 2 -
> Reconnaissance Traffic Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 3 -
> Command and Control Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 4 -
> Lateral Movement Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
Remediate
List of Services
-
> Block IPList Item 1
-
> Modify Blacklists Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 2 -
> Freeze AD Account Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 3 -
> EDR Quarantine Endpoint Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 4
Recover
List of Services
-
> Monitor for backdoors and re-attacksList Item 1
-
> Be informed when your network returns to normal operations Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 2 -
> AI learns from each event to improve detection of future threats Write a description for this list item and include information that will interest site visitors. For example, you may want to describe a team member's experience, what makes a product special, or a unique service that you offer.
List Item 3
Simple, Affordable, Effective Ransomware Defense
Designed specifically to meet the needs of resource constrained teams, Cyber Security Shield combines AI, Automation and Continuous Monitoring to detect and surface ransomware attacks without overloading your team with noisy alerts and false positives. Intuitive and easy to operate, your team can quickly identify and stop ransomware before it causes damage.
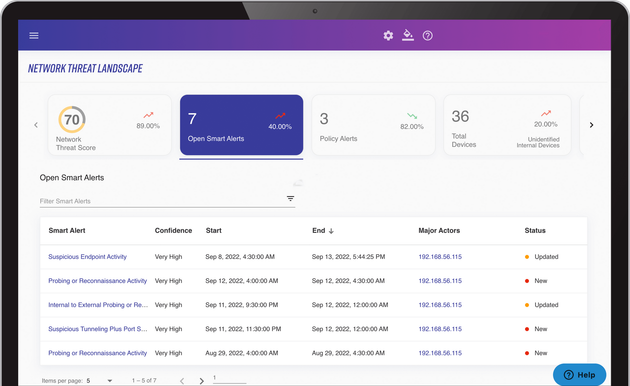
Intelligent, Real-time Alerting
Cyber Security Shield uses artificial intelligence to learn your network’s normal patterns and deliver Smart Alerts – prioritized by threat and risk. Cyber Security Shield emulates human thinking and contextualizes the nature of the threat in relation to the value of your assets.
Our alerting capability allows you to get ahead of ransomware attacks.
The Data Your Defenders Need
Cyber Security Shield provides all of the information necessary to detect and respond to ransomware attacks. The analysis of the event artifacts enabled by Cyber Security Shield leads to quicker remediation of attacks and reduces the likelihood of the organization falling victim to ransomware payments.
A simple truth: resource constrained teams can't operate a SIEM.
Security Information and Event Management (SIEM) tools were supposed to answer the lack of visibility across security tools and paint a clear picture of a company's security posture. The reality is they are too expensive and too complicated for many organizations to operate.
Cyber Security Shield eXtended Cloud Security delivers a cost-effective cloud and network detection, response, and compliance solution for business. When combined with an endpoint defense tool, the solution will meet 100% of the detection, remediation, and compliance needs of medium and small organizations at a fraction of the cost.

Low TCO, Effective Threat Detection and Remediation
Where a SIEM requires multiple, costly security analyst to review and clear events, AI risk prioritizes security events so that your small team only focuses on what is important. Cyber Security Shield correlates AD, Network, M365, Azure, AWS, Threat Intelligence and EDR threat streams to surface what is important.
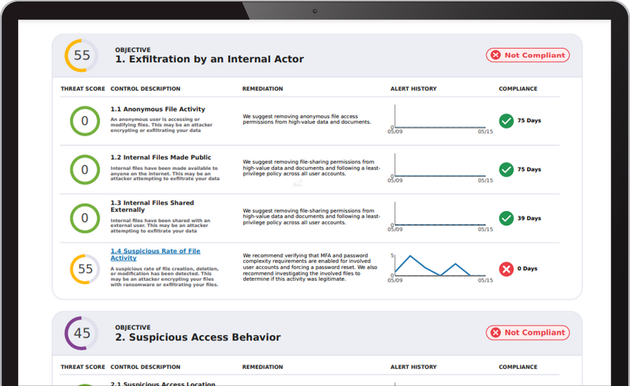
No Hardware or Software to Deploy and Manage
SIEM systems are built for the large enterprise, requiring extensive IT support. Cyber Security Shield is a 100% cloud-native SaaS solution. It pulls data from your existing systems (firewalls, EDR, AD, routers and switches) and requires little to no IT support to operate.
Your Attack Surface Has Expanded. What’s Your Next Move?
The increase in remote working is here to stay, and cybercriminals have exploited that shift. Businesses are struggling to monitor their expanded attack surface and it is now paramount that every business can fully secure its VPN & Cloud environments to protect its most critical data assets.
Cyber Security Shield
provides the protection required to thwart increasingly frequent and sophisticated cyberattacks originating through remote workers. Our unique ability to gather and correlate AD/Azure, M365, VPN, RDP and Network logs for risks and threats allows you to quickly and easily adapt your cybersecurity approach to the changing dynamics of remote working.

VPN & Network Labeling
Label high-risk networks and design policies that emphasize protection of these subnetworks and address ranges. You can also label networks that should be seeing no outside activity to highlight potential unauthorized access.

AI-Based Threat Analytics and Alerts
Ingest VPN logs into NDaaS to power AI-based analysis of threats and alerts on suspicious or anomalous events, such as unusual access times or locations and unusual number of failed logins.
Unique Policies for Your Remote Workforce
CX NDaaS provides all of the information necessary for incident response against cyberattack. Authentication and access policies that monitor cloud user activities and remote network access quickly surface protentional threats.

Fast and Easy to Deploy
NDaaS is up and running in minutes with no additional hardware or software required. It integrates seamlessly with your existing cybersecurity tools and can be entirely managed remotely.
CX NDaaS quickly plugs into your firewall, creating a powerful SaaS network defense solution.
CX NDaaS connects to your firewall in under 30 minutes, requires no on-promise hardware.
Your firewall plus CX NDaaS allows IT & Security teams to see risks across your network, detect cyberattacks like ransomware, and automatically remediate attacks 24X7 without the need for a SIEM or SOAR. Utilizing advanced AI, reduces false positives and focuses teams on the risks and threats that matter.

Award Winning AI Risk and Threat Detection
The CX NDaaS AI engine utilizes unsupervised machine learning in a big data architecture with integrated policy engine to detect, correlate and surface risk, vulnerabilities and indicators of compromise across your hybrid network. Integrated remediation means one click to stop an attack night or day.

Simple and Inexpensive to Deploy and Operate
Cloud-native SaaS mean rapid deployment and simple operations. Continuously monitor your network and cloud 24X7 without having to add new headcount and spend money and time on complex product training.
Single inclusive platform including reporting
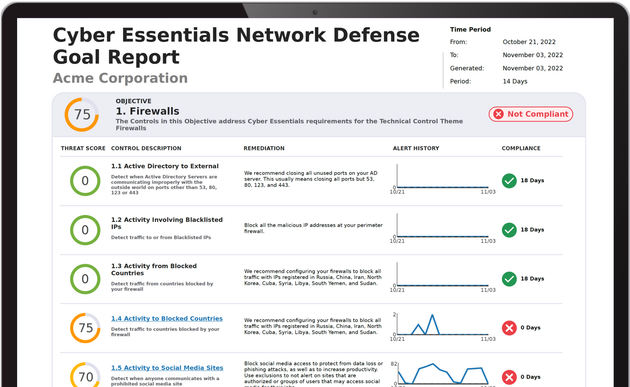
The CX NDaaS Platform is a complete hybrid network defense system that includes a full reporting capability. Automated reports include; network risk scorecard, executive reports, ransomware defense reports, and M365/Azure risk and threat reports.
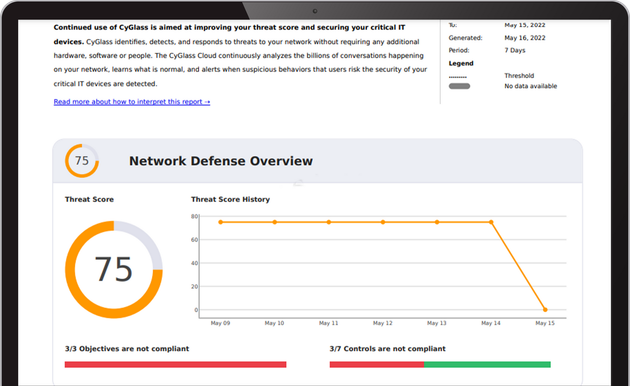
CX NDaaS includes over a hundred Compliance Controls mapped to Automated Compliance Reports.
CX NDaaS reports are easily configurable and provide continuous automated regulatory compliance.
Reports include ISO-27001, NIST 800-53, NIST-171/CMMC, UK Cyber Essentials, and easily configurable control mapping and report creation for Insurance Audit Compliance and industry regulatory compliance like Motion Picture Association (MPAA), CIS Critical Security Controls, and IEEE standards.

Automated Continuous Compliance
Whether proving audit compliance for security frameworks like NIST and ISO standards, industry standards like Motion Picture Association (MPA), or constantly changing supply chain audits from multiple ecosystem partner audits, CX NDaaS has you covered. The CX NDaaS platform includes over one hundred AI-refined internet, network, cloud, and directory cybersecurity controls.
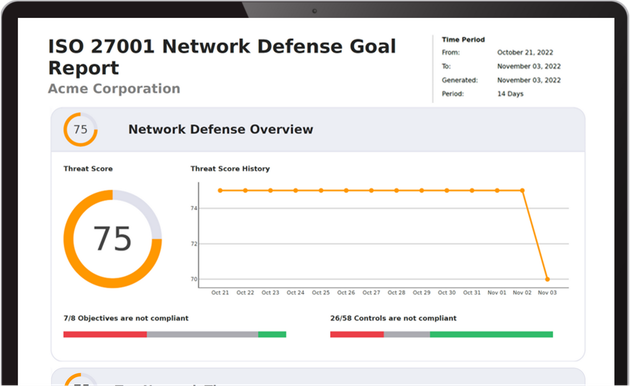
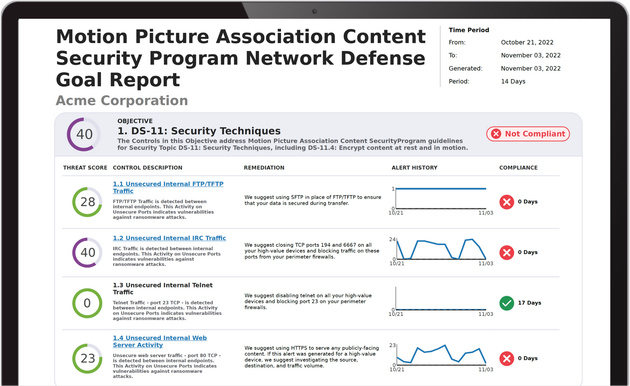
CX NDaaS Reporting Engine
Both the eXtended Cloud Security, and Hybrid Network Defense Cloud solutions include the CX NDaaS automated reporting engine, hundreds of out-of-the box controls, and simple to understand, actionable report templates.
Out-Of-The-Box Compliance Reports
The CX NDaaS platform includes easily configurable compliance report templates for ISO-27001, NIST 800-53, NIST 171/CMMC, UK Cyber Essentials, CISA Ransomware Defense, Cyber Insurance Compliance, Supply Chain Compliance, as well as specialty compliance for standards like Motion Picture Association (MPA).
Can you protect your supply chain if your network is attacked?
Digital transformation has connected businesses together to create unparalleled efficiency in accuracy and volume of transactions, removing boundaries between companies’ systems and processes for ever. There is unfortunately a downside, this web of interconnected systems has opened opportunities for cyber criminals to enter via the weakest links and navigate the digital supply chain to their intended target via the connected eco-system.
Larger organizations within these digital supply chains are adopting zero-trust models, forcing their smaller partners to embrace stronger cybersecurity programs and most importantly mandating them to demonstrate adherence using data and KPI’s – continuous compliance.

Defend Your Network and Defend Your Supply Chain
From weak application security to exploiting identity errors in Microsoft Azure, supply chain attackers use vulnerabilities for one organization in the ecosystem to gain silent entry into and attack other more prominent organizations. With Cyber Security shield eXtended Cloud Defense, IT and security teams can monitor, detect and contain attacks that originate in their network, or migrate silently from a partner's network.

Demonstrate Continuous Compliance
Implement, report, and remain compliant with cybersecurity standards set and enforced by ecosystem partners, auditors, and associations. Rapidly advance security hygiene while demonstrating continuous compliance to win and maintain lucrative supply chain contracts.